本サイトは、快適にご利用いただくためにクッキー(Cookie)を使用しております。
Cookieの使用に同意いただける場合は「同意する」ボタンを押してください。
なお本サイトのCookie使用については、「個人情報保護方針」をご覧ください。
IDA Pro has a feature of cooperating with Bochs virtual machine that enables users to analyze code executed before an operating system is booted up. Recently I had an opportunity to test this feature in practice. This post shows how to use this feature in a real-life scenario.
A few months ago, my co-worker gave me a copy of Petya ransomware that gained attention for its low level feature of encrypting MBRs. Even though I'm not a malware analyst, as a reverse engineering enthusiast, I thought I would try analyzing some of the code with IDA.
First off, I uploaded the binary to VirusTotal to make sure it's a true copy of Petya. Then I ran it on my victim machine running Windows 7. The machine rebooted immediately after installation and after a fake chkdisk, an ASCII art of a skull appeared on a red screen.
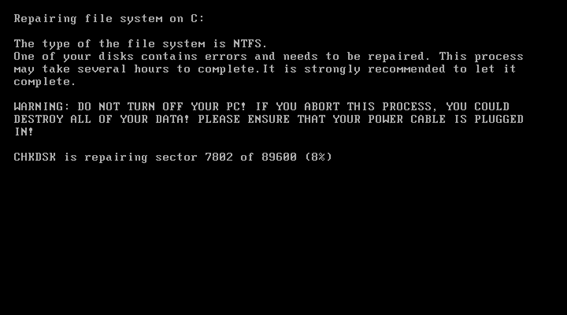

Cool. That's what's expected of Petya. Then I specified the copy of the flat hard disk image as a boot disk image of the Bochs emulator. Again, the skull showed up. That meant the infected MBR was running properly on Bochs.
Next, I loaded the bochsrc configuration file into IDA. It automatically selected IDA loader appropriately and showed the disassembled code in MBR. I could start debugging the code under the Bochs debugger and see how it worked.
Bochs plugin for IDA is a neat way of analyzing low level code such as MBR and bootloader using IDA. It should be useful not only for reverse engineers but OS developers.
Happy reversing!
おすすめ記事