本サイトは、快適にご利用いただくためにクッキー(Cookie)を使用しております。
Cookieの使用に同意いただける場合は「同意する」ボタンを押してください。
なお本サイトのCookie使用については、「個人情報保護方針」をご覧ください。
REvil Master Key leaks in attacking Kaseya, and introduces REvil Decryptor patching process
We confirmed that the Russian hacker forum leaked a Master Key that the ransomware "REvil" used to attack Kaseya. The Master Key can be used to decrypt files that were encrypted by the REvil.
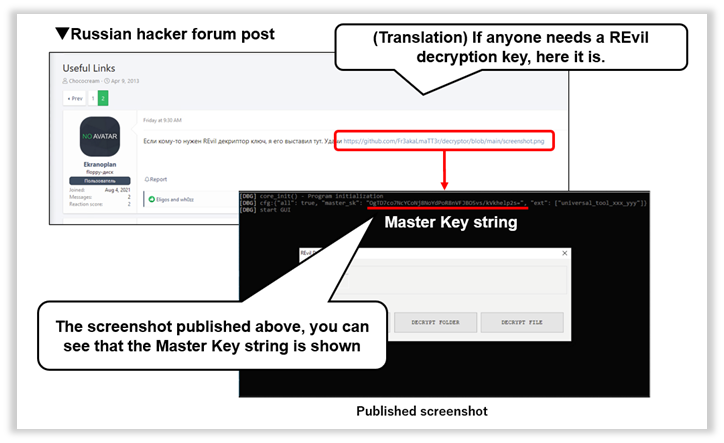
Fig. 1 - Master Key String Published in the Russian Hacker Forum
Only one screenshot was posted in the forum above, but as you can see that the Master Key string (below) appears in the image.
・Master Key of REvil: OgTD7co7NcYCoNj8NoYdPoR8nVFJBO5vs/kVkhelp2s =
However, executable decryption tool “REvil Decryptor” also appears in the screenshot, is not publicly available and should be obtained separately, because it is usually provided only to those victims who were attached by the REvil and paid ransom money.
We have discovered that "REvil Decryptor", which seems to have been passed on to the victim organization in some past REvil attacks, has been uploaded to VirusTotal. By directly rewriting the binary of "REvil Decryptor", it was confirmed that the above master key is actually valid in the environment infected with the sample used in the attack on Kaseya. Here is the detailed patch steps to decrypt files.
■How to decrypt files encrypted by the REvil
In order to decrypt files that were encrypted by the REvil specimen used in the attack to Kaseya, we confirmed that the leaked Master Key works in the following process.
(1) Obtain the REvil Decryptor on VirusTotal that may have been handed to victim organizations
(2) Directly over-write binary data to replace existing decryption key with the Master Key.
(3) Execute REvil Decryptor to decrypt all encrypted files.
As mentioned earlier, the decryption tool "REvil Decryptor" executable file is not publicly available, but we confirmed that several decryption tools that may have been used in previous attacks have been uploaded on VirusTotal. The "REvil Decryptor" that we obtained and used in this report has following hash values.
・The hash value of REvil Decryptor used for this validation:
7f22aa88a120780e5f59ca74f31a2aec49883a60c5ea39131d98075735e93108
The above REvil Decryptor is assumed to be a decryption tool that has been previously distributed to any damage organization, and REvil Decryptor binaries contain unique decryption key for each victim organization.
Therefore, since it cannot be used as is, open the above REvil Decryptor in a binary editor, then identify the place where the existing decryption key is embedded (in this case, 0x10200).
Then, over-write the relevant part with the binary editor to the following contents including the character string of the Master Key.
{"all":true,"master_sk":"OgTD7co7NcYCoNj8NoYdPoR8nVFJBO5vs/kVkhelp2s=","ext":["0a42wro"]}
Note that the suffix "0a42wro" varies depending on the environment and is described according to the extension of the file that was actually encrypted. (In this report we used “0a42wro” because it happened to be "0a42wro" at the time of this verification.)
Specifically, the binary is rewritten (patched) as shown in the image below.
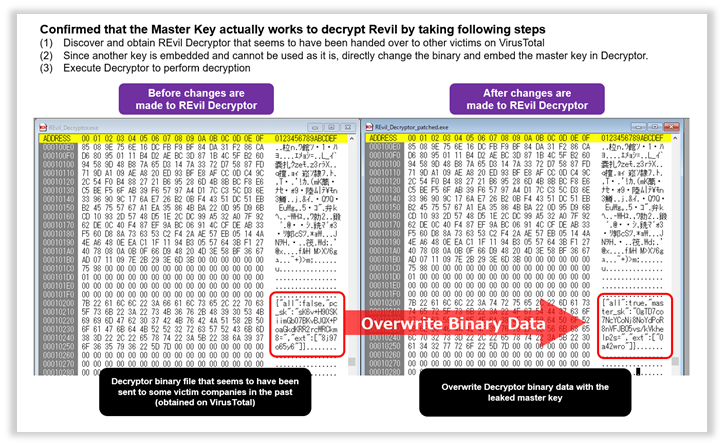
Fig. 2 - Before and After Binary Rewriting (Patching) REvil Decryptor
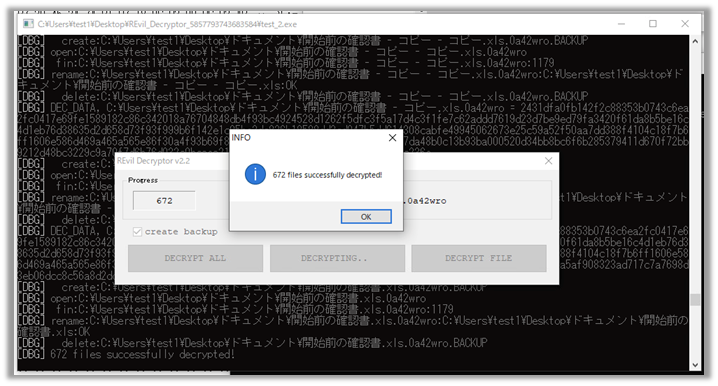
We prepared a PC infected by the specimen used for attacking Kaseya, and verified with the patched REvil Decryptor, and confirmed that all decoding succeeded as shown in the following Figure.
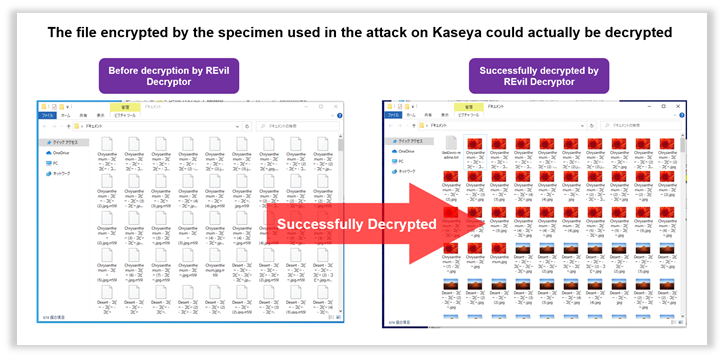
Fig. 3 - A file encrypted with a patched REvil Decryptor has been decrypted
Following Figure shows an example of a successful decryption (encrypted with the specimen used to attack Kaseya) performed by the patched REvil Decryptor.
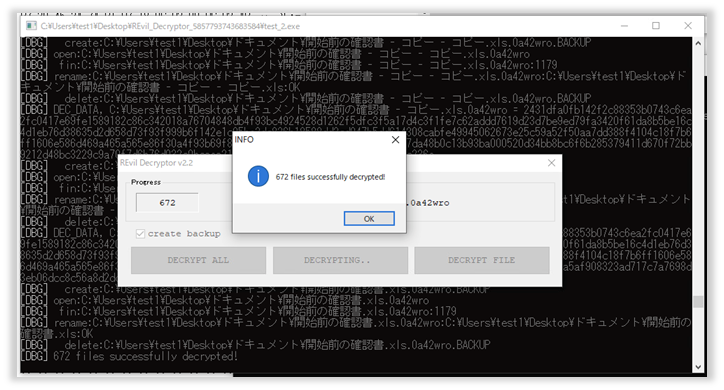
Fig. 4 - Successful decryption of a file encrypted by a patched REvil Decryptor
We confirmed that the published Master Key perfectly works for the files that were encrypted by the specimen used in attacking Kaseya.
However, in an environment infected with REvil specimens used outside the attack on Kaseya, it is also confirmed that the encrypted file cannot be decrypted using this Master Key (see the Fig. below). It is important to note that the leaked Master Key does not mean that all REvil victims can be relieved. (* Valid keys for REvil specimens other than Kaseya are called "Operator Keys" and not "Master Keys". They are unknown at this point of time.)
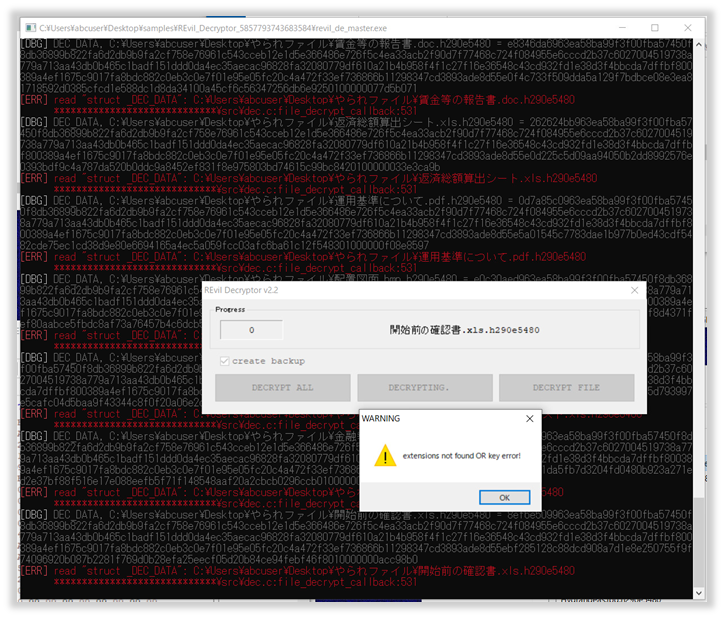
Fig. 5 - Cannot decrypt files if the REvil infection happened outside Kaseya.
おすすめ記事