本サイトは、快適にご利用いただくためにクッキー(Cookie)を使用しております。
Cookieの使用に同意いただける場合は「同意する」ボタンを押してください。
なお本サイトのCookie使用については、「個人情報保護方針」をご覧ください。
DVRF is a router firmware for Linksys E1550 designed for learning embedded device security. It contains some simple target binaries vulnerable to common attacks like stack buffer overflow, command injection, etc. What makes exploiting these binaries different is that they are compiled for 32bit little-endian MIPS processors.
Installing DVRF on Linksys E1550 is damn easy (pun intended). You only have to navigate to the Firmware Upgrade page and upload the DVRF image, DVRF_v02.bin. However, to run the binaries you have to physically access the serial port (UART) and log into the console. It may be a bit harder for those who are not familiar with hardware hacking as you have to do some soldering work on the PCB.
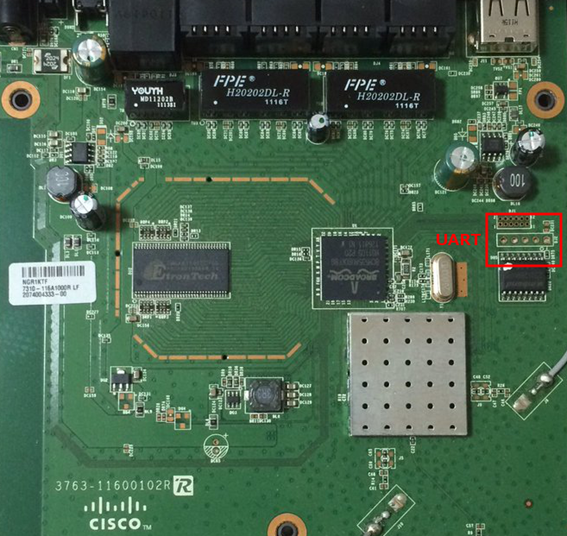
Fig.1 Linksys E1550 Serial Port
If you successfully connect to the serial port, you'll see some boot messages as shown below and then be logged into the console. The target binaries are under /pwnable.
Release memory for upgrade file. file=[/tmp/Success_u_s.asp_new], length=[97451] file=[/tmp/Fail_u_s.asp_new], length=[97058] http upgrading....umount all disks cmd=[write /tmp/uploadn43NJK linux ] find "linux" in MTD 1 (0xfb0000) Max support length = 16449536 Upgrading code pattern correct! ................freeram=[46825472] bufferram=[585728] The free memory is enough, writing image once. .(4042)(2896)............................... .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. ................(3704).....(2688)..(3392)....(992)................... .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. ....(3096)(2896)............................................ .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. .................................................. ............................................(1957) finish loading the F/W, wait for the mtd_write finish! sum=[7753728] linux: CRC OK Writing image to flash, waiting a monent... done Sending SIGTERM to all processes Sending SIGKILL Restarting system. Start to blink diag led ... CFE version 5.60.127.11 based on BBP 1.0.37 for BCM947XX (32bit,SP,LE) Build Date: Sun Mar 20 12:13:21 CST 2011 (david@CBT-CSCB) Copyright (C) 2000-2008 Broadcom Corporation. ...(snip)... BusyBox v1.7.2 (2016-01-19 10:42:40 CST) built-in shell (msh) Enter 'help' for a list of built-in commands. # # ls -R /pwnable/ /pwnable/: Intro ShellCode_Required /pwnable/Intro: README heap_overflow_01 stack_bof_01 uaf_01 /pwnable/ShellCode_Required: README socket_bof socket_cmd stack_bof_02 #
Now, let's exploit one of these binaries. stack_bof_02 is a small program that just strcpy() its first command line argument to a buffer on the stack without checking the length and consequently results in a buffer overflow. The following is a disassembly of the vulnerable code. It should be trivial how the vulnerability is triggered.
.text:004008AC lw $v0, 0x150+arg_4($fp) .text:004008B0 nop .text:004008B4 addiu $v0, 4 .text:004008B8 lw $v0, 0($v0) .text:004008BC nop .text:004008C0 move $v1, $v0 .text:004008C4 addiu $v0, $fp, 0x150+var_138 .text:004008C8 move $a0, $v0 # dest .text:004008CC move $a1, $v1 # src .text:004008D0 la $t9, strcpy .text:004008D4 nop .text:004008D8 jalr $t9 ; strcpy
You can create a payload on your laptop and then download it into /tmp of Linksys E1550 with wget. The message 'PWNED!' is printed as a result of executing system() as shown below. The details were intentionally omitted to avoid spoiling the fun of exploitation.
# ls /tmp/ payload # # ./pwnable/ShellCode_Required/stack_bof_02 xxx Welcome to the Second BoF exercise! You'll need Shellcode for this! ;) You entered xxx Try Again # # cat /tmp/payload | xargs ./pwnable/ShellCode_Required/stack_bof_02 Welcome to the Second BoF exercise! You'll need Shellcode for this! ;) You entered AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA▒$▒@DDDDDDDDDDDDDDDD▒▒@BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB▒<▒@CCCC▒r▒@ Try Again PWNED! #
After playing with DVRF, you can restore the stock firmware from the Web interface.
MIPS is quite different in many ways from Intel x86 family and it looked weird for me at first sight, but it doesn't mean that it's more difficult to exploit.
References:
[1] Getting Started with Damn Vulnerable Router Firmware (DVRF) v0.1
https://www.praetorian.com/blog/getting-started-with-damn-vulnerable-router-firmware-dvrf-v0.1
[2] GitHub - praetorian-inc/DVRF
おすすめ記事